Subject content
This subject content should be taught within a range of realistic contexts based around the major themes in the specification. To gain the most from the specification, a number of the sections will benefit from being taught holistically. For example, algorithms could be taught alongside programming techniques as there is a close relationship between them.
The specification content in Sections 3.1–3.8 is presented in a two-column format. The left hand column contains the specification content that all students must cover and that is assessed in the written papers. The right hand column exemplifies the additional information that teachers will require to ensure that their students study the topic in an appropriate depth and, where appropriate, gives teachers the parameters in which the subject will be assessed.
The skills, knowledge and understanding from all of the subject content within the specification will be assumed in all assessments. Both assessments may contain synoptic questions that will require students to use their skills, knowledge and understanding from across the entire specification. For example, whilst the understanding of binary numbers will be directly assessed in paper 2, the underlying knowledge and principles may be indirectly required for questions in paper 1.
For exams from 2022, we will support the following programming languages:
- C#
- Python (version 3)
- VB.NET.
In paper 1 students will be required to design, write, test and refine program code in one of the three languages above. In preparation for paper 1, students should have sufficient practical experience of:
- structuring programs into modular parts with clear documented interfaces to enable them to design appropriate modular structures for solutions
- including authentication and data validation systems/routines within their computer programs
- writing, debugging and testing programs to enable them to develop the skills to articulate how programs work and argue using logical reasoning for the correctness of programs in solving specified problems
- designing and applying test data (normal, boundary and erroneous) to the testing of programs so that they are familiar with these test data types and the purpose of testing
- refining programs in response to testing outcomes.
In preparation for paper 2 students should have sufficient practical experience of writing and refining SQL.
Students should be given as much opportunity as possible to practise their programming skills in the school or college's chosen language and SQL.
Fundamentals of algorithms
Representing algorithms
|
Content |
Additional information |
|---|---|
|
Understand and explain the term algorithm. |
An algorithm is a sequence of steps that can be followed to complete a task. Be aware that a computer program is an implementation of an algorithm and that an algorithm is not a computer program. |
|
Understand and explain the term decomposition. |
Decomposition means breaking a problem into a number of sub-problems, so that each sub-problem accomplishes an identifiable task, which might itself be further subdivided. |
|
Understand and explain the term abstraction. |
Abstraction is the process of removing unnecessary detail from a problem. |
|
Use a systematic approach to problem solving and algorithm creation representing those algorithms using pseudo-code, program code and flowcharts. |
Any exam question where students are given pseudo-code will use the AQA standard version. Exam questions will indicate the form of response expected. For example, pseudo-code, program code or a flowchart. |
|
Explain simple algorithms in terms of their inputs, processing and outputs. |
Students must be able to identify where inputs, processing and outputs are taking place within an algorithm. |
|
Determine the purpose of simple algorithms. |
Students should be able to use trace tables and visual inspection to determine how simple algorithms work and what their purpose is. |
Efficiency of algorithms
|
Content |
Additional information |
|---|---|
|
Understand that more than one algorithm can be used to solve the same problem. |
|
|
Compare the efficiency of algorithms explaining how some algorithms are more efficient than others in solving the same problem. |
Formal comparisons of algorithmic efficiency are not required. Exam questions in this area will only refer to time efficiency. |
Searching algorithms
|
Content |
Additional information |
|---|---|
|
Understand and explain how the linear search algorithm works. |
Students should know the mechanics of the algorithm. |
|
Understand and explain how the binary search algorithm works. |
Students should know the mechanics of the algorithm. |
|
Compare and contrast linear and binary search algorithms. |
Students should know the advantages and disadvantages of both algorithms. |
Sorting algorithms
|
Content |
Additional information |
|---|---|
|
Understand and explain how the merge sort algorithm works. |
Students should know the mechanics of the algorithm. |
|
Understand and explain how the bubble sort algorithm works. |
Students should know the mechanics of the algorithm. |
|
Compare and contrast merge sort and bubble sort algorithms. |
Students should know the advantages and disadvantages of both algorithms. |
Programming
Students need a theoretical understanding of all the topics in this section for the paper 1 exam even if the programming language(s) taught does not support all of the topics. Exams will always present algorithms using the current version of the AQA pseudo-code. The document can be found on the AQA website.
Students need a practical understanding of all the topics and skills in this section for the paper 1 exam. When they are writing computer programs in an exam they will need to ensure they use meaningful identifier names, use suitable data types and that all logic flow is clearly identifiable to examiners.
Exam questions will explicitly state in what form the response needs to be provided. This will be, for example, pseudo-code, program code or a flowchart, and students must respond as instructed. Where pseudo-code is an accepted method of response, students may present their answers to questions in any suitable format and do not need to use the AQA pseudo-code.
Data types
Content | Additional information |
|---|---|
Understand the concept of a data type. | |
Understand and use the following appropriately:
| Depending on the actual programming language(s) being used, these data types may have other names. For example real numbers may be described as float. In exams we will use the general names given opposite. |
Programming concepts
Content | Additional information |
|---|---|
Use, understand and know how the following statement types can be combined in programs:
| The three combining principles (sequence, iteration/repetition and selection/choice) are basic to all high-level imperative programming languages. Students should be able to write programs using these statement types. They should be able to interpret and write algorithms that include these statement types. Students should know why named constants and variables are used. |
Use definite (count controlled) and indefinite (condition controlled) iteration, including indefinite iteration with the condition(s) at the start or the end of the iterative structure. | A theoretical understanding of condition(s) at either end of an iterative structure is required, regardless of whether they are supported by the language(s) being used. An example of definite (count controlled) iteration would be: FOR i ← 1 TO 5 … Instructions here … ENDFOR An example of indefinite (condition controlled) iteration with the condition at the start would be: WHILE NotSolved … Instructions here … ENDWHILE Examples of indefinite (condition controlled) iteration with the condition at the end would be: REPEAT … Instructions here … UNTIL Solved DO … Instructions here … WHILE NotSolved |
Use nested selection and nested iteration structures. | An example of nested iteration would be: WHILE NotSolved
… Instructions here ...
FOR i ← 1 TO 5
… Instructions here …
ENDFOR
… Instructions here …
ENDWHILEAn example of nested selection would be: IF GameWon THEN
… Instructions here …
IF Score > HighScore THEN
… Instructions here …
ENDIF
… Instructions here …
ENDIF |
Use meaningful identifier names and know why it is important to use them. | Identifier names include names for variables, constants and subroutine names. |
Arithmetic operations in a programming language
|
Content |
Additional information |
|---|---|
|
Be familiar with and be able to use:
|
Integer division, including remainders, is usually a two stage process and uses modular arithmetic: eg the calculation 11/2 would generate the following values: Integer division: the integer quotient of 11 divided by 2 (11 DIV 2) = 5 Remainder: the remainder when 11 is divided by 2 (11 MOD 2) = 1 |
Relational operations in a programming language
|
Content |
Additional information |
|---|---|
|
Be familiar with and be able to use:
|
Students should be able to use these operators within their own programs and be able to interpret them when used within algorithms. Note that different languages may use different symbols to represent these operators. |
Boolean operations in a programming language
|
Content |
Additional information |
|---|---|
|
Be familiar with and be able to use:
|
Students should be able to use these operators, and combinations of these operators, within conditions for iterative and selection structures. |
Data structures
|
Content |
Additional information |
|---|---|
|
Understand the concept of data structures. |
It may be helpful to set the concept of a data structure in various contexts that students may already be familiar with. It may also be helpful to suggest/demonstrate how data structures could be used in a practical setting. |
|
Use arrays (or equivalent) in the design of solutions to simple problems. |
Only one and two-dimensional arrays are required. |
|
Use records (or equivalent) in the design of solutions to simple problems. |
An example of a record definition would be: RECORD Car make : String model : String reg : String price : Real noOfDoors : Integer ENDRECORD |
Input/output
|
Content |
Additional information |
|---|---|
|
Be able to obtain user input from the keyboard. |
|
|
Be able to output data and information from a program to the computer display. |
String handling operations in a programming language
|
Content |
Additional information |
|---|---|
|
Understand and be able to use:
|
Expected string conversion operations:
|
Random number generation in a programming language
|
Content |
Additional information |
|---|---|
|
Be able to use random number generation. |
Students will be expected to use random number generation within their computer programs. An understanding of how pseudo-random numbers are generated is not required. |
Structured programming and subroutines (procedures and functions)
|
Content |
Additional information |
|---|---|
|
Understand the concept of subroutines. |
Students should know that a subroutine is a named ‘out of line’ block of code that may be executed (called) by simply writing its name in a program statement. |
|
Explain the advantages of using subroutines in programs. |
|
|
Describe the use of parameters to pass data within programs. |
Students should be able to use subroutines that require more than one parameter. Students should be able to describe how data is passed to a subroutine using parameters. |
|
Use subroutines that return values to the calling routine. |
Students should be able to describe how data is passed out of a subroutine using return values. |
|
Know that subroutines may declare their own variables, called local variables, and that local variables usually:
|
|
|
Use local variables and explain why it is good practice to do so. |
|
| Describe the structured approach to programming. |
Students should be able to describe the structured approach including modularised programming, clear well-documented interfaces (local variables, parameters) and return values. Teachers should be aware that the terms arguments and parameters are sometimes used but in examinable material we will use the term parameter to refer to both of these. |
| Explain the advantages of the structured approach. |
Robust and secure programming
|
Content |
Additional information |
|---|---|
|
Be able to write simple data validation routines. |
Students should be able to use data validation techniques to write simple routines that check the validity of data being entered by a user. The following validation checks are examples of simple data validation routines:
|
|
Be able to write simple authentication routines. |
Students should be able to write a simple authentication routine that uses a username and password. Students will only be required to use plain text usernames and passwords (ie students will not need to encrypt the passwords). |
|
Understand what is meant by testing in the context of algorithms and programs. Be able to correct errors within algorithms and programs. |
|
Understand what test data is and describe the following types of test data:
|
Boundary data would be for example: If the allowed range is 1 to 10, then boundary data is 0, 1, 10, 11, ie either side of the allowed boundary. |
|
Be able to select and justify the choice of suitable test data for a given problem. |
|
Understand that there are different types of error:
|
|
| Be able to identify and categorise errors within algorithms and programs. |
Fundamentals of data representation
Number bases
|
Content |
Additional information |
|---|---|
|
Understand the following number bases:
|
|
|
Understand that computers use binary to represent all data and instructions. |
Students should be familiar with the idea that a bit pattern could represent different types of data including text, image, sound and integer. |
|
Explain why hexadecimal is often used in computer science. |
Converting between number bases
|
Content |
Additional information |
|---|---|
|
Understand how binary can be used to represent whole numbers. |
Students must be able to represent decimal values between 0 and 255 in binary. |
|
Understand how hexadecimal can be used to represent whole numbers. |
Students must be able to represent decimal values between 0 and 255 in hexadecimal. |
|
Be able to convert in both directions between:
|
The following equivalent maximum values will be used:
|
Units of information
|
Content |
Additional information |
|---|---|
|
Know that:
|
A bit is either a 0 or a 1.
|
|
Know that quantities of bytes can be described using prefixes. Know the names, symbols and corresponding values for the decimal prefixes:
Be able to compare quantities of bytes using the prefixes above. |
Students might benefit from knowing that historically the terms kilobyte, megabyte, etc have often been used to represent powers of 2. The International System of Units (SI units) kilo, mega and so forth refer to values based on powers of 10. When referring to powers of 2 the terms kibi, mebi and so forth would normally be used but students do not need to know these. |
Binary arithmetic
|
Content |
Additional information |
|---|---|
|
Be able to add together up to three binary numbers. |
Students will need to be able to add together up to three binary numbers using a maximum of 8 bits per number. Students will only be expected to add together a maximum of three 1s in a single column. Answers will be a maximum of 8 bits in length and will not involve carrying beyond the 8th bit. |
|
Be able to apply a binary shift to a binary number. |
Students will be expected to use a maximum of 8 bits. Students will be expected to understand and use only a logical binary shift. Students will not need to understand or use fractional representations. |
|
Describe situations where binary shifts can be used. |
Binary shifts can be used to perform simple multiplication/division by powers of 2. |
Character encoding
|
Content |
Additional information |
|---|---|
|
Understand what a character set is and be able to describe the following character encoding methods:
|
Students should be able to use a given character encoding table to:
|
|
Understand that character codes are commonly grouped and run in sequence within encoding tables. |
Students should know that character codes are grouped and that they run in sequence. For example in ASCII ‘A’ is coded as 65, ‘B’ as 66, and so on, meaning that the codes for the other capital letters can be calculated once the code for ‘A’ is known. This pattern also applies to other groupings such as lower case letters and digits. |
|
Describe the purpose of Unicode and the advantages of Unicode over ASCII. Know that Unicode uses the same codes as ASCII up to 127. |
Students should be able to explain the need for data representation of different alphabets and of special symbols allowing a far greater range of characters. It is not necessary to be familiar with UTF-8, UTF-16 or other different versions of Unicode. |
Representing images
Content | Additional information |
|---|---|
Understand what a pixel is and be able to describe how pixels relate to an image and the way images are displayed. | Students should know that the term pixel is short for picture element. A pixel is a single point in an image. |
Describe the following for bitmaps:
Know that the size of a bitmap image is measured in pixels (width x height). | The size of an image is expressed directly as width of image in pixels by height of image in pixels using the notation width x height. Colour depth is the number of bits used to represent each pixel. |
Describe how a bitmap represents an image using pixels and colour depth. | Students should be able to explain how bitmaps are made from pixels. |
Describe using examples how the number of pixels and colour depth can affect the file size of a bitmap image. | Students should be able to describe how higher numbers of pixels and higher colour depths can affect file size, and should also be able to use examples. |
Calculate bitmap image file sizes based on the number of pixels and colour depth. | Students only need to use colour depth and number of pixels within their calculations. Size = (bits) = W x H x D Size = (bytes) = (W x H x D)/8 W = image width H = image height D = colour depth in bits. |
Convert binary data into a bitmap image. | Given a binary pattern that represents a simple bitmap, students should be able to draw the resulting image as a series of pixels. |
Convert a bitmap image into binary data. | Given a simple bitmap, students should be able to write down a bit pattern that represents the image. |
Representing sound
|
Content |
Additional information |
|---|---|
|
Understand that sound is analogue and that it must be converted to a digital form for storage and processing in a computer. |
|
|
Understand that analogue signals are sampled to create the digital version of sound. |
Students should understand that a sample is a measure of amplitude at a point in time. |
|
Describe the digital representation of sound in terms of:
|
Sampling rate is the number of samples taken in a second and is usually measured in hertz (1 hertz = 1 sample per second). Sample resolution is the number of bits per sample. |
|
Calculate sound file sizes based on the sampling rate and the sample resolution. |
File size (bits) = rate x res x secs rate = sampling rate res = sample resolution secs = number of seconds |
Data compression
|
Content |
Additional information |
|---|---|
|
Explain what data compression is. Understand why data may be compressed and that there are different ways to compress data. |
Students should understand that it is common for data to be compressed and should be able to explain why it may be necessary or desirable to compress data. |
|
Explain how data can be compressed using Huffman coding. Be able to interpret Huffman trees. |
Students should be familiar with the process of using a tree to represent the Huffman code. |
|
Be able to calculate the number of bits required to store a piece of data compressed using Huffman coding. Be able to calculate the number of bits required to store a piece of uncompressed data in ASCII. |
Students should be familiar with carrying out calculations to determine the number of bits saved by compressing a piece of data using Huffman coding. |
|
Explain how data can be compressed using run length encoding (RLE). |
Students should be familiar with the process of using frequency/data pairs to reduce the amount of data stored. |
|
Represent data in RLE frequency/data pairs. |
Students could be given a bitmap representation and they would be expected to show the frequency and value pairs for each row, eg 0000011100000011 would become 5 0 3 1 6 0 2 1. |
Computer systems
Hardware and software
|
Content |
Additional information |
|---|---|
|
Define the terms hardware and software and understand the relationship between them. |
Boolean logic
|
Content |
Additional information |
|---|---|
|
Construct truth tables for the following logic gates:
|
Students do not need to know about or use NAND and NOR logic gates. |
|
Construct truth tables for simple logic circuits using combinations of NOT, AND, OR and XOR gates. Interpret the results of simple truth tables. |
Students should be able to construct truth tables which contain up to three inputs. |
Create, modify and interpret simple logic circuit diagrams. Students will only need to use NOT, AND, OR and XOR gates within logic circuits. Students will be expected to understand and use the following logic circuit symbols: 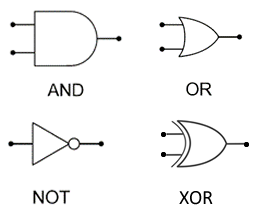 |
Students should be able to construct simple logic circuit diagrams which contain up to three inputs. |
|
Create and interpret simple Boolean expressions made up of NOT, AND, OR and XOR operations. |
Students will be expected to understand and use the following Boolean
expression operators:
For example the expression (A AND B) OR (NOT C) would be represented as: |
|
Create the Boolean expression for a simple logic circuit. Create a logic circuit from a simple Boolean expression. |
Software classification
Content | Additional information |
|---|---|
Explain what is meant by:
Give examples of both types of software. | Students should understand that:
|
Understand the need for, and functions of, operating systems (OS) and utility programs. Understand that the OS handles management of the:
|
Classification of programming languages and translators
| Content | Additional information |
|---|---|
Know that there are different levels of programming language:
Explain the main differences between low-level and high-level languages. | Students should understand that most computer programs are written in high-level languages and be able to explain why this is the case. |
Know that machine code and assembly language are considered to be low-level languages and explain the differences between them. |
Students should be able to:
|
Understand that all programming code written in high-level or assembly languages must be translated. Understand that machine code is expressed in binary and is specific to a processor or family of processors. | |
Understand the advantages and disadvantages of low-level language programming compared with high-level language programming. | |
Understand that there are three common types of program translator:
Explain the main differences between these three types of translator. Understand when it would be appropriate to use each type of translator. |
Students will need to know that:
|
Systems architecture
Content | Additional information |
|---|---|
Explain the role and operation of main memory and the following major components of a central processing unit (CPU) within the Von Neumann architecture:
| A bus is a collection of wires through which data/signals are transmitted from one component to another. Knowledge of specific registers is not required. |
Explain the effect of the following on the performance of the CPU:
| |
Understand and explain the Fetch-Execute cycle. | The CPU continually reads instructions stored in main memory and executes them as required:
|
Understand the different types of memory within a computer:
Know what the different types of memory are used for and why they are required. | |
Understand the differences between main memory and secondary storage. Understand the differences between RAM and ROM. | Students should be able to explain the terms volatile and non-volatile. Main memory will be considered to be any form of memory that is directly accessible by the CPU (except for cache and registers). Secondary storage is considered to be any non-volatile storage mechanism not directly accessible by the CPU. |
Understand why secondary storage is required. | |
Be aware of different types of secondary storage (solid state, optical and magnetic). Explain the operation of solid state, optical and magnetic storage. Discuss the advantages and disadvantages of solid state, optical and magnetic storage. | Students should be aware that SSDs use electrical circuits to persistently store data but will not need to know the precise details such as use of NAND gates. |
Explain the term cloud storage. | Students should understand that cloud storage uses magnetic and/or solid state storage at a remote location. |
Explain the advantages and disadvantages of cloud storage when compared to local storage. | |
Understand the term embedded system and explain how an embedded system differs from a non-embedded system. | Students must be able to give examples of embedded and non-embedded systems. |
Fundamentals of computer networks
Content | Additional information |
|---|---|
Define what a computer network is. Discuss the advantages and disadvantages of computer networks. | |
Describe the main types of computer network including:
| PAN – only Bluetooth needs to be considered. LAN – know that these usually cover relatively small geographical areas. LAN – know that these are often owned and controlled/managed by a single person or organisation. WAN – know that the Internet is the biggest example of a WAN. WAN – know that these usually cover a wide geographic area. WAN – know that these are often under collective or distributed ownership. |
Understand that networks can be wired or wireless. Discuss the advantages and disadvantages of wireless networks as opposed to wired networks. | Students should know that wired networks can use different types of cable such as fibre and copper and when each would be appropriate. |
Describe the following common LAN topologies:
| Students should be able to draw topology diagrams and describe the differences between the two topologies. They should also be able to select the most appropriate topology for a given scenario. |
Define the term network protocol. | |
Explain the purpose and use of common network protocols including:
| Students should know what each protocol is used for (eg HTTPS provides an encrypted version of HTTP for more secure web transactions). Students should understand that Ethernet is a family of related protocols rather than a single protocol. They do not need to know the individual protocols that make up the Ethernet family. Students should understand that Wi-Fi is a family of related protocols rather than a single protocol. They do not need to know the individual protocols that make up the Wi-Fi family but they should know that Wi-Fi is a trademark and that the generic term for networks of this nature is WLAN. |
Understand the need for, and importance of, network security. | |
Explain the following methods of network security:
| Students should be able to explain, using examples, what each of these security methods is and when each could be used. Students should understand how these methods can work together to provide a greater level of security. The capabilities of firewalls have changed dramatically in recent years and will continue to do so. Students should be aware that a firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Students should understand that MAC address filtering allows devices to access, or be blocked from accessing a network based on their physical address embedded within the device’s network adapter. |
Describe the 4 layer TCP/IP model:
Understand that the HTTP, HTTPS, SMTP, IMAP and FTP protocols operate at the application layer. Understand that the TCP and UDP protocols operate at the transport layer. Understand that the IP protocol operates at the internet layer. | Students should be able to name the layers and describe their main function(s) in a networking environment. Application layer: this is where the network applications, such as web browsers or email programs, operate. Transport layer: this layer sets up the communication between the two hosts and they agree settings such as the size of packets. Internet layer: addresses and packages data for transmission. Routes the packets across the network. Link layer: this is where the network hardware such as the NIC (network interface card) is located. OS device drivers also sit here. Teachers should be aware that the link layer is sometimes referred to as the network access layer or network interface layer. However, students will not be expected to know these alternative layer names. |
Cyber security
Fundamentals of cyber security
|
Content |
Additional information |
|---|---|
|
Be able to define the term cyber security and be able to describe the main purposes of cyber security. |
Students should know that cyber security consists of the processes, practices and technologies designed to protect networks, computers, programs and data from attack, damage or unauthorised access. |
Cyber security threats
Updated
We've updated the phrases 'white-box penetration test' and 'black-box penetration test' in the 'Additional information' column below.
Content | Additional information |
|---|---|
Understand and be able to explain the following cyber security threats:
| Pharming is a cyber attack intended to redirect a website's traffic to a fake website. |
Explain what penetration testing is and what it is used for. | Penetration testing is the process of attempting to gain access to resources without knowledge of usernames, passwords and other normal means of access. Students should understand the following two types of penetration testing:
|
Social engineering
|
Content |
Additional information |
|---|---|
|
Define the term social engineering. Describe what social engineering is and how it can be protected against. Explain the following forms of social engineering:
|
Students should know that social engineering is the art of manipulating people so they give up confidential information. Blagging is the act of creating and using an invented scenario to engage a targeted victim in a manner that increases the chance the victim will divulge information or perform actions that would be unlikely in ordinary circumstances. Phishing is a technique of fraudulently obtaining private information, often using email or SMS. Shouldering is observing a person's private information over their shoulder eg cashpoint machine PIN numbers. |
Malicious code (malware)
|
Content |
Additional information |
|---|---|
|
Define the term malware. Describe what malware is and how it can be protected against. Describe the following forms of malware:
|
Malware is an umbrella term used to refer to a variety of forms of hostile or intrusive software. |
Methods to detect and prevent cyber security threats
|
Content |
Additional information |
|---|---|
Understand and be able to explain the following security measures:
|
Relational databases and structured query language (SQL)
Relational databases
| Content | Additional information |
|---|---|
Explain the concept of a database. | |
Explain the concept of a relational database. | |
Understand the following database concepts:
Understand that the use of a relational database facilitates the elimination of data inconsistency and data redundancy. | Note that whilst the terms entity, attribute and entity identifier are more commonly used when an abstract model of a database is being considered, the terms given here will be used for both implementations of and abstract models of databases. |
Structured query language (SQL)
| Content | Additional information |
|---|---|
Be able to use SQL to retrieve data from a relational database, using the commands:
| Exam questions will require that data is extracted from no more than two tables for any one query. |
Be able to use SQL to insert data into a relational database using the commands. INSERT INTO table_name (column1, column 2 …) VALUES (value1, value2 …) Be able to use SQL to edit and delete data in a database using the commands. UPDATE table_name SET column1 = value1, column2 = value2 ... WHERE condition DELETE FROM table_name WHERE condition |
Ethical, legal and environmental impacts of digital technology on wider society, including issues of privacy
|
Content |
Additional information |
|---|---|
|
Explain the current ethical, legal and environmental impacts and risks of digital technology on society. Where data privacy issues arise these should be considered. |
Exam questions will be taken from the following areas:
Students will be expected to understand and explain the general principles behind the issues rather than have detailed knowledge on specific issues. Students should be aware that ordinary citizens normally value their privacy and may not like it when governments or security services have too much access. Students should be aware that governments and security services often argue that they cannot keep their citizens safe from terrorism and other attacks unless they have access to private data. |
